We all know that iOS 5.0.1 untethered jailbreak for non-A5 devices has been officially released by the Chronic Dev team and the iPhone Dev team, but do you know how to perform it on you device?
Saturday, 31 December 2011
Google's winter surprise: Searching 'let it snow' brings snow flakes down the page
To activate the feature and to see for yourself how the snow falls onto the Google Search results you simply need to type “let it snow” into your Google Search results and the snow will start falling.
You can also use your mouse pointer like a finger on cold glass to 'write' on your Google window.
Do a barrel roll: Google's best Easter eggs
It takes care of more than 1billion searches worldwide every day but Google still finds time to make our lives more fun.
Google search: do a barrel roll
See the magic for yourself.
MiniTool Partition Wizard Bootable CD
As partitioning tools go, MiniTool's is quite friendly. Users are taken through a step by step process, making partition creation, management, and even recovery literally as easy as 1-2-3.
Faster picture access
Normally with the camera, you have to tap the icon of the camera roll in the lower left corner to access the images. But with iOS 5, you just swipe left to right and you quickly go into the camera roll. To get back to the camera, just swipe right to left and when you get to the last picture, you're back in camera mode.
Split/Un-dockable Keyboard on the iPad
So Apple split the keyboard in half and moved the two halves to the edges of the screen. This works in both landscape and portrait modes.
You split the keyboard by placing both thumbs in the middle of the screen on the keyboard and pulling them apart. The keyboard will then resize and float slightly, as well as become translucent.
Check App Usage
This will be especially handy for those of us with 16GB iPhones and iPads. My phone is near capacity and I have more than a few apps that were downloaded and forgotten. If your iDevice is filling up, check in Settings, General and Usage to see how much space each app is taking up.
User-Defined Keyboard Shortcuts
iOS 5 has something similar. Go into your Settings menu, pick General, then Keyboard. At the bottom is a prompt to add a new shortcut. Just type in the word or phrase that deserves a shortcut, and then plug in the shortcut itself.
It won't spare you the embarrassment of Autocorrect's interesting and dubious choices, but it will make typing easier and faster.
Assistive Touch
But it's not limited to the disabled. Anyone can make custom gestures for their own use. For example, you swipe left to right to unlock the phone. Well, you could make a custom swipe from right to left to lock the phone.
Create custom vibrations and LED flashes
First up is personalized vibration. Go into Settings, General, Accessibility, and turn on Custom Vibrations. Then choose someone from your Contacts list, select Edit, where you will see Vibration right below Ringtone. Choose from the collection or create a new vibration that you can tap on the phone.
Second is LED flash alerts. Turn this on in the same location as custom vibrations. When you set your phone to silent mode, you'll get blinking notifications through screen flashes instead of a vibration or sound.
Take pictures with your headphones
Now, users can take pictures by tapping on the volume increase button on their headphones. This may seem trivial, but it does make the iPhone 4S a point-and-shoot camera. It also gives you a few feet of room because you no longer have to hold the camera up to your face to take a picture. You can use the length of the headphones wire to take a picture.
Big Safari upgrades
* Hide your activity: Launch settings and find Safari. Select Enable for the Private Browsing tab. The browser will no longer record everything you do and pull up the last page you visited every time you open the app. You can also clear your history from settings.
* If you remember Lynx, the text-based browser for Unix shell, then you will like Reader, a feature that strips all the junk out of a Web site and shows just the text, similar to Readability and Instapaper add-ons for desktop browsers. Look in the URL window after a page loads, and you will see a gray button marked "Reader." Tap it and the page is rendered without the other junk.
Dig Deeper into iOS 5
Apple has proclaimed more than 200 new features in iOS 5, from the over-the-air updates (about damn time) to the Newsstand app to iMessage allowing you to bypass the texting limits of carriers, there's a lot to like in this new OS.
Still, some great features manage to slip by that deserve special highlight, which we will do. Also, keep an eye on this thread on MacRumors, where people are accumulating all the little features they find.
Friday, 30 December 2011
AVG Rescue CD
Like the Avira Antivir Rescue System, the AVG Rescue CD is a bootable
(what else?) CD that lets you clear infections completely from your PC.
All recovery actions are done independent of your computer's installed
OS, meaning even the best viruses and malware won't survive the purge.
TestDisk
We've featured Recovery is Possible earlier in this list. TestDisk is
one of the utilities packaged in that recovery CD. In case you forgot
what it does: it lets users recover damaged or accidentally deleted
partitions.
Pandora Recovery
In many ways Pandora Recovery is just like Recuva, allowing deleted file recovery without the trouble of booting from a Linux CD. But Pandora Recovery is designed to run without any installation, which means you can copy it to a USB drive, and run it on any computer.
Download
Recuva
Sometimes you just want to recover a deleted file, but you don't want to go through the trouble of booting from a recovery CD. That's where Recuva comes in. It just looks are the empty space on your PC's drive—which still contains the information stored in the files you've deleted accidentally, and rebuilds the lost data based on what it finds.
PING (PartImage is Not Ghost)
The great thing about PING is that it goes beyond mere recovery.
Included in the bootable CD/USB drive are tools that let you back up
entire partitions and BIOS configuration data. You can even use PING to
delete the password for the computer's admin.
Avira Antivir Rescue System
It's a common case: PCs so badly infected that they can no longer boot up properly, or stay infected despite the best efforts of anti-virus and -malware programs. Avira Antivir Rescue System simply launches its own version of Linux, which makes it possible to clean everything without any trouble.
Recovery is Possible (RIP)
Here's another boot CD that does what it says—puts hard disk data recovery tools within reach of even basic users. Included in the package is TestDisk, a utility that recovers deleted partitions, and PhotoRec, an undelete tool that goes beyond just retrieving deleted images.
PC CMOS Cleaner
Forgot your BIOS password? You can PC CMOS Cleaner to reset it, and regain access to that important configuration tool on your computer. If it's a x86 or x86_64 (64-bit) PC, CMOS Cleaner is most likely compatible with your BIOS.
Download
Never say never, especially about recovering lost data
As computers become more important at our work, home, and school, so has data. Many times we consider the information we store on our PCs more crucial than actual physical objects. And why not, when the files we work with on the computer represent hours of hard work?
It's still amazing how many users take a flippant approach towards backing up important data—if they bother maintaining redundancies at all. The following software won't replace any good backup regime, but they do provide a chance that information lost through human or machine error won't be lost forever.
Wednesday, 28 December 2011
Android Assistant

Top 18 features to help you easily and efficiently manage your android phone.
Android Assistant is one of the most powerful and comprehensive management tools to improve your android phone's performance. It speeds up your phone's running speed and saves battery.
【Top18 features】
1. Monitor status (cpu, memory, battery)
2. Process Manager (Auto Boost and Quick Boost can distinguish different types of processes thus will not kill fatal system processes and apps in Ignore List.)
3. Cache Cleaner
4. System Clean(Browser History, Clipboard, Market History, Gmail History, Google Earth History, Google Map History)
5. Save Battery Settings(bluetooth, wifi, gps, auto-sync, orientation, haptic feedback, screen brightness, timeout)
6. File Manager
7. Startup Manager
8. Batch Uninstall
9. Battery use
10. Volume Control
11. Ringer
12. Startup Time
13. Startup Silent(Menu->Settings->Startup Silent)
14. System Info
15. Widget(Quick Booster[1,4], Shortcuts[4])
16. App 2 SD(Support android2.2 and later):Get more free internal phone storage space
17. Batch Installation
18. App backup and restore
DOWNLOAD
Screenshots:

Saturday, 17 December 2011
Close all open applications with one click
Usually I would manually close each application. Depending on the number of open applications this can be a waste of time. The people at NTWind Software have a perfect utility for this situation aptly called Close All Windows. Instead of manually closing each application just click the Close All Windows button on your taskbar.
In this article I will show you how to install and configure Close All Windows on your computer for easy access on the taskbar.
In this article I will show you how to install and configure Close All Windows on your computer for easy access on the taskbar.
To get started head over to NTWind Software and download the latest version of Close All Windows.
After the file is downloaded extract the CloseAll folder to a permanent location on your computer. Since Close All Windows is an application I extracted the folder to C:\Program Files\ where applications are typically installed.
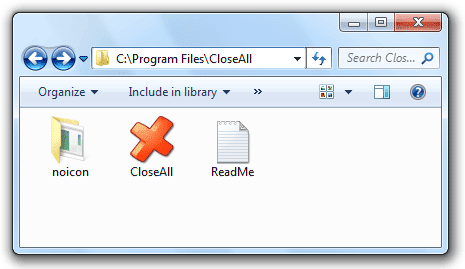

For easy access it is best to pin the application to the taskbar. Drag the Close All Windows application from the CloseAll folder onto the taskbar.
Wednesday, 14 December 2011
Create a Shortcut Key for any application
You can create your own custom key combination in keyboard to launch any application.
In order to do that:
1. Right click on the application shortcut/icon, go to properties.
2. Note where it says “Shortcut Key”. Enter your combination here.
For example:
“Ctrl+Alt+U”
The choice is purely up to you.
3. Click OK. Your shortcut is now effective! Just hit that key combination and your application will be
launched.
You can also shutdown the computer by pressing your own keys but you will have to create a Shutdown shortcut first. To learn that go to:
Create Shutdown Icon
After creating the Shutdown icon you may shutdown the system using keyboard by giving your own custom key combination to the shortcut as mentioned above.
Happy Tweaking!
Fastest way to Lock Computer
Just press:
Winkey + L
Winkey + L
View System Up Time
To view the amount of time that your computer has been running with out rebooting or restarting the computer:
1) Open the Command Prompt (located under Accessories)
2) Type 'systeminfo' (without the dashes)
3) Once the system has finished gathering the information, scroll up and the time is displayed in the System Up Time/System Boot Time field.
As you can see, running systeminfo also gives a lot of useful information.
Nameless folder
To create a nameless folder:
Create a new folder and when asked to type in the name, Leave it blank.
As you can see.. it wont let you.
However if you press:
ALT + 255
the folder will appear to not have a name.
Useful for hiding the folder. If you change the folder icon to a suitable one, it won't be found by other users.
On old windows 98 boxes, this wont work unless you create it under command prompt, but in this case you won't be able to access the folder/files inside unless you know the exact name to be used in command prompt.
Create a new folder and when asked to type in the name, Leave it blank.
As you can see.. it wont let you.
However if you press:
ALT + 255
the folder will appear to not have a name.
Useful for hiding the folder. If you change the folder icon to a suitable one, it won't be found by other users.
On old windows 98 boxes, this wont work unless you create it under command prompt, but in this case you won't be able to access the folder/files inside unless you know the exact name to be used in command prompt.
Enabling/Disabling Automatic Logon
1. Click Start on the Windows taskbar, and then click Run.
2. In the Open box, type:
control userpasswords2
then click OK.
3. In the dialog box that appears,
You'll see: "Users must enter a user name and password to use this computer" check box.
Enabled will require users to logon, disabling will make Windows automatically logon to the Administrator account.
Windows Automated Installation Kit for Windows 7
Applies To: Windows 7, Windows Server 2008 R2
The Windows® Automated Installation Toolkit (AIK) is a collection of tools and documentation designed to help IT Professionals deploy Windows.
The Windows AIK is ideal for highly customized environments. The tools in the AIK enable you to configure many deployment options, and they provide a high degree of flexibility. The corporate deployment environment varies from one company to another. Depending on your business needs and resources, you may choose to use all or parts of the resources available in the AIK.
Download the Windows AIK tools from this Microsoft web site:(http://go.microsoft.com/fwlink/?LinkId=136976)
For the latest information about this release, see the Windows Automated Installation Kit for Windows 7 Readme.
Tools Included with the Windows AIK
The following table shows the important tools that are included with the Windows AIK.
Windows System Image Manager (Windows SIM):
The tool used to open Windows images, create answer files, and manage distribution shares and configuration sets.
ImageX:
The tool used to capture, create, modify, and apply Windows images.
Deployment Image Servicing and Management (DISM):
The tool used to apply updates, drivers, and language packs to a Windows image. DISM is available in all installations of Windows 7 and Windows Server 2008 R2.
Windows Preinstallation Environment (Windows PE):
A minimal operating system environment used to deploy Windows. The AIK includes several tools used to build and configure Windows PE environments.
User State Migration Tool (USMT):
A tool used to migrate user data from a previous Windows operating system to Windows 7. USMT is installed as part of the AIK in the %PROGRAMFILES%\Windows AIK\Tools\USMT directory. For more information about USMT, see the User State Migration Tool User’s Guide (%PROGRAMFILES%\Windows AIK\Docs\Usmt.chm).
Creating a Shutdown/Reboot/Logoff Icon
Windows XP has a file called SHUTDOWN.EXE which allows you to easily create icons to shutdown or restart your computer.
To create a shutdown shortcut on the desktop:
Right click on an open area of the desktop
Select New / Shortcut
Enter the following:
shutdown.exe -s -t 00
Press the Next button
For the name, enter in anything you like. I just use shutdown. Click on the Finish button.
For a reboot, enter: shutdown -r -t 00
For a logoff, enter: shutdown -l -t 00
Shutdown [{-l|-s|-r|-a}] [-f] [-m [\\ComputerName]] [-t xx] [-c "message"] [-d[u][p]:xx:yy]
Parameters
-l - Logs off the current user, this is also the defualt. -m ComputerName takes precedence.
-s - Shuts down the local computer.
-r - Reboots after shutdown.
-a - Aborts shutdown. Ignores other parameters, except -l and ComputerName. You can only use -a during the time-out period.
-f - Forces running applications to close.
-m [\\ComputerName] - Specifies the computer that you want to shut down.
-t xx - Sets the timer for system shutdown in xx seconds. The default is 20 seconds.
-c "message" - Specifies a message to be displayed in the Message area of the System Shutdown window. You can use a maximum of 127 characters. You must enclose the message in quotation marks.
Monday, 5 December 2011
File Sharing in Linux Using Samba
Share folders in Red Hat Enterprise Linux using Samba so that it can be accessed from a computer using Windows.
Packages required:
samba
samba-common
samba-client
samba-doc
Add a new user using useradd:
#useradd jethin
#passwd jethin
Create samba password for users using smbpasswd command:
#smbpasswd -a <username>
#smbpasswd -e <username>
eg:
#smbpasswd -a jethin
then give password.
#smbpasswd -e jethin
Add the following to the configuration file in /etc/samba/smb.conf
[Folders]
comment = linux shares
path = /
public = yes
browseable = yes
writable = yes
printable = no
valid users = jethin
hosts allow = 192.168.1.
Packages required:
samba
samba-common
samba-client
samba-doc
Add a new user using useradd:
#useradd jethin
#passwd jethin
Create samba password for users using smbpasswd command:
#smbpasswd -a <username>
#smbpasswd -e <username>
eg:
#smbpasswd -a jethin
then give password.
#smbpasswd -e jethin
Add the following to the configuration file in /etc/samba/smb.conf
[Folders]
comment = linux shares
path = /
public = yes
browseable = yes
writable = yes
printable = no
valid users = jethin
hosts allow = 192.168.1.
The above details can be edited according to your necessity.
Next Step:
Start the daemons:
smb,smbpasswd
Start or restart the services:
#service smb restart
To load samba on Startup:
#chkconfig smbpasswd on
Now you will be able to access all files in / from the windows computer.
Now you will be able to access all files in / from the windows computer.
Just type the ip of the linux system in Start-> run(in Windows system).
eg: \\192.168.1.112
Then type the username and samba password which you created.
Then type the username and samba password which you created.
Friday, 2 December 2011
Hack the root's password in Red Hat Enterprise Linux 6
Hack the root's password in RHEL6
1. Press 'a' as soon as you see the boot menu.
A screenshot is given below:
2. In the next screen you can see a command line. Tap the 'spacebar'
3. Press '1' or 's'.
4. Then press enter.
The system will enter the single user mode.
After sometime when the shell appears, Type the following command:
5. passwd -d root
6. Then press Enter.
Your root's password has been removed.
Now restart the system and Enjoy!
Friday, 9 September 2011
Ultrasurf, browse the web anonymously
UltraSurf is a free software which enables users inside countries with
heavy Internet censorship to visit any public web sites in the world
safely and freely. Users in countries without internet censorship also
use it to protect their internet privacy and security.
With UltraSurf started, you can use web browsers (like IE, Firefox) the same as before, but all are under UltraSurf's protection now.
DOWNLOAD
Features include:
Privacy: Protect Internet privacy with anonymous surfing and browsing -- hide IP addresses and locations, clean browsing history, cookies etc...
Security: Completely transparent data transfer and high level encryption of the content allow you to surf the web with high security.
Now if you’re thinking how is Ultrasurf able to bypass censorship, the answer isn’t simple. They use a technology that allows it to pass through firewall protections and give you access (encrypted) to the internet – because it can pass through firewalls, some antiviruses will label it as a Trojan, but only because of its behavior not due to malicious code.
With UltraSurf started, you can use web browsers (like IE, Firefox) the same as before, but all are under UltraSurf's protection now.
DOWNLOAD
Features include:
Privacy: Protect Internet privacy with anonymous surfing and browsing -- hide IP addresses and locations, clean browsing history, cookies etc...
Security: Completely transparent data transfer and high level encryption of the content allow you to surf the web with high security.
Now if you’re thinking how is Ultrasurf able to bypass censorship, the answer isn’t simple. They use a technology that allows it to pass through firewall protections and give you access (encrypted) to the internet – because it can pass through firewalls, some antiviruses will label it as a Trojan, but only because of its behavior not due to malicious code.
Disable User Account Control (UAC) the Easy Way in Win 7
Windows 7 makes it much easier to deal with UAC settings than vista, and in fact you don’t have to completely disable UAC if you don’t want to. Just type UAC into the start menu or Control Panel search box.
You can simply drag the slider up or down, depending on how often you want to be alerted:
If you drag it all the way down to the bottom, UAC will be disabled entirely.
Thursday, 8 September 2011
Restore Dell™ Computer with Microsoft® Windows® 7 to Its Original Setup or a Recovery Point with Norton Ghost™
- Verify the modem or network cable is detached from the computer.
- Start the computer.
- As the computer starts, press <F8> on the keyboard until the Advanced Boot Options menu appears on the screen.
- Press the <Down Arrow> on the keyboard to select Repair Your Computer on the Advanced Boot Options menu, and then press <Enter>.
- Specify the language settings that you want, and then click Next.
- Log in as a user who has administrative credentials, and then click OK
- Click Dell Factory Image Restore.
- In the Dell Factory Image Restore window, click Next.
- Click to select the Yes, reformat hard drive and restore system software to factory condition check box.
- Click Next.
The computer is restored to the default factory configuration. - When the restore operation is completed, click Finish to restart the computer.The software is now installed as it was when the computer was first received.
Friday, 12 August 2011
Install any Windows Operating System With a USB Flash Drive
Windows is used in most of the Laptops and Netbooks but how do you install it without a CD drive?
Use a USB flash drive in place of the DVD. In this article I will show you how to create a bootable USB flash drive that will install Windows so you can install Windows on any computer without an optical drive.
Before we get started you will need:
The link below redirects you to a free utility that will automatically make a bootable USB flash drive from a Windows ISO image file.
Windows_USB_Setup
Simply download the tool, specify the location of your ISO file and the wizard will do everything for you.
A screenshot of the software is given below:
For any assistance contact me : jethinshaji@gmail.com
Use a USB flash drive in place of the DVD. In this article I will show you how to create a bootable USB flash drive that will install Windows so you can install Windows on any computer without an optical drive.
Before we get started you will need:
- Windows (XP\7\vista\2003\2008) ISO file
- 4GB USB flash drive.
The link below redirects you to a free utility that will automatically make a bootable USB flash drive from a Windows ISO image file.
Windows_USB_Setup
Simply download the tool, specify the location of your ISO file and the wizard will do everything for you.
A screenshot of the software is given below:
For any assistance contact me : jethinshaji@gmail.com
Wednesday, 3 August 2011
Restore file/folder to previous version in Win 7 without using any additional software
Restoring was very difficult for earlier version of windows. We had to go through a lot of steps and finally we will get a whole backup(including many unwanted files or we won't get the specific backup we wanted.
NOW in Windows 7 we can easily restore the pics we have deleted from a folder by just taking the properties of that folder as shown below:
With just one click we can get what we thought was lost forever.
To do that we have to make sure that we have enabled the restore option.
To enable the system restore option,
Take the My Computer properties as shown in figure:
Then click system protection as shown above.
In the box that appears you can select which drives need to be protected as shown in figure below:
We have to make sure that the restore points are created occasionally to restore whenever we want.
My Operating System is Windows 7 Ultimate. I think it works in all Win 7 versions.
Win 7 Ultimate is the best OS for personal use.
Friday, 29 July 2011
Boost Your System Performance By Selective Startup
There are a lot of Startup items in your Windows OS which are loaded automatically. Most of them won't be needed for you. So when they are loaded, it decreases your system performance. You can manually disable them and increase the speed of your computer to a great extent.
You may start doing this by taking:
Start Run
Run
Type "msconfig" in the box as shown in fig:
When you press OK, a box appears and in that box choose the Selective Startup option as shown in fig:
Then choose startup from the Upper Tab and it will show the list of all startup items.
Now you may select only the startup items which you need and exclude the rest as shown in fig:
After selecting, u gotta Click OK and restart your system for the changes to get effective.
This is a simple thing which most people already know.
I've just posted to help Beginners.
This will increase your system performance to a great extent.
You may start doing this by taking:
Start
Type "msconfig" in the box as shown in fig:
When you press OK, a box appears and in that box choose the Selective Startup option as shown in fig:
Then choose startup from the Upper Tab and it will show the list of all startup items.
Now you may select only the startup items which you need and exclude the rest as shown in fig:
After selecting, u gotta Click OK and restart your system for the changes to get effective.
This is a simple thing which most people already know.
I've just posted to help Beginners.
This will increase your system performance to a great extent.
Sunday, 24 July 2011
Intel Itanium Processors
Intel Itanium Processors
Intel® Itanium® processor-based servers deliver robust performance for UNIX and mainframe environments and support today's most demanding business applications. With superior virtualization performance and more virtual machines per server, Intel Itanium processors offer scalability for your most complex, data-intensive workloads.
Scalable servers powered by Intel® Itanium® processors enable system configurations of as many as 512 processors and a full petabyte (1024 TB) of RAM. With full support for both 32-bit and 64-bit applications, the capacity of these processors provides unmatched flexibility in tailoring systems to your enterprise needs.
- Superior, built-for-virtualization performance with more virtual machines per server
- Optimizes server efficiency with twice as many processing cores
- Delivers up to eight times more physical memory capacity over previous generation¹
- Increases core utilization with up to six times more memory bandwidth than previous generation¹
- Supports real-time workload balancing
- Support for up to 16 sockets while providing low voltage options
INTEL ITANIUM PROCESSOR 9300 SERIES
Scalable servers powered by Intel® Itanium® processors enable system configurations of as many as 512 processors and a full petabyte (1024 TB) of RAM. With full support for both 32-bit and 64-bit applications, the capacity of these processors provides unmatched flexibility in tailoring systems to your enterprise needs.
Saturday, 23 July 2011
Access Pen Drive safely without being affected by a Virus even without the help of an Antivirus
There are many methods to access a pen drive and remove the virus in it without being affected by the virus.
I'm talking about the way to access it even without installing any antivirus.
THE FIRST 4 STEPS ARE TO BE DONE ONLY ONCE IN YOUR COMPUTER.
THE FIRST 4 STEPS ARE TO BE DONE ONLY ONCE IN YOUR COMPUTER.
At first you have to disable all Autoplay features permanently in your computer.
For that,
- Open the GPO editor as i discussed in my earlier post GPO Editing.
- In the User Configuration
Administrative Templates
Windows Components
Autoplay policies, Enable all the settings as shown in the figure below:
- Then save and close it.
- In the Folder Options, Enable "Show hidden Files and Folders" as shown in the figure below:
- Then Click Start
Run and type the drive letter of your pen drive and press enter. An example is shown in the figure below:
- Now you can see the virus files in the pen drive. Delete them permanently by using shift+delete.
YOU JUST HAVE TO DO THE LAST 2 STEPS ONLY.
Friday, 22 July 2011
Group Policy Object Editing
Group Policy Object Editing allows you to have complete control over your computer.
- You can make your system look the way you want.
- Restrict others from using their pen drives without your permission (which helps in preventing your system from virus infections especially if you are staying in a hostel).
- Hide or restrict specific Drives(C,D...) or block them so that others won't use or view your stuff......
If you would like to learn such tweaks and use them Scroll down and read this post.
In order to do that,
1. Take run and type mmc
2. Click file and choose Add/Remove snap in
3. From the Box that just appeared, choose Group Policy Object Editor and click Add
4. In the Box that just appeared Click “Browse”.
5. Then select the users tab.
You can see the list of users in your computer.
6. Select a user other than your user account so that you will have full privileges and you can restrict the other person the way you want .
7. Click OK.
8. Click Finish.
9. GPO is ready to be edited.
10. Double click the settings you want to use and click enable->OK
11. Whatever edits you do will be affecting the user you selected only.
12. After editing just save it.
13. Next time onwards you just have to open the file you have saved and you can edit it easily.
14. If you want to use it for a different user you will have to select a new user next time and start from the beginning.
Subscribe to:
Comments (Atom)